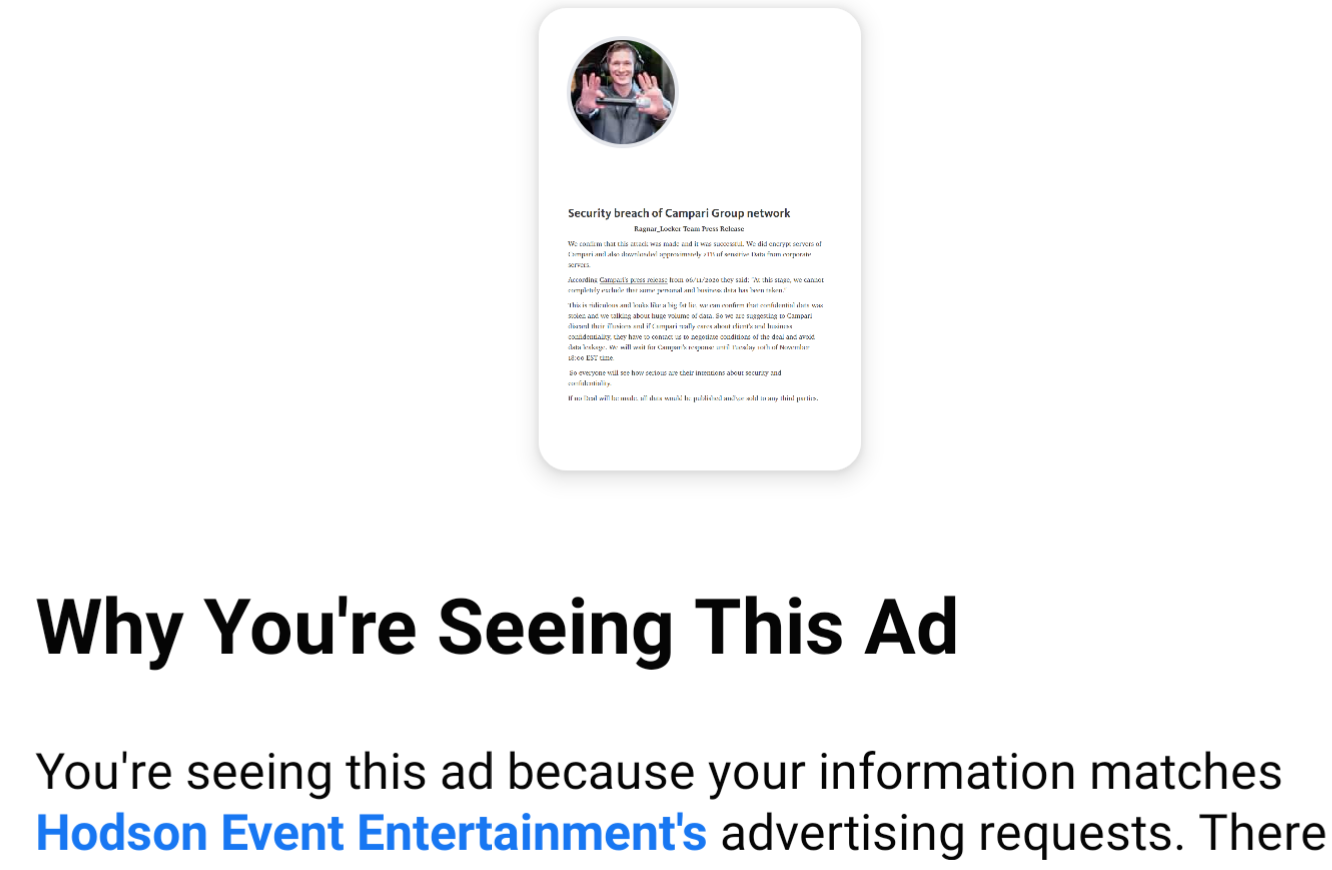
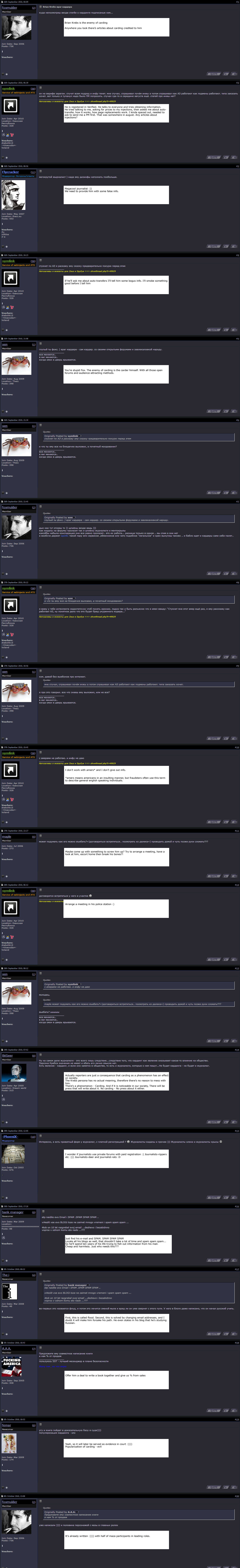
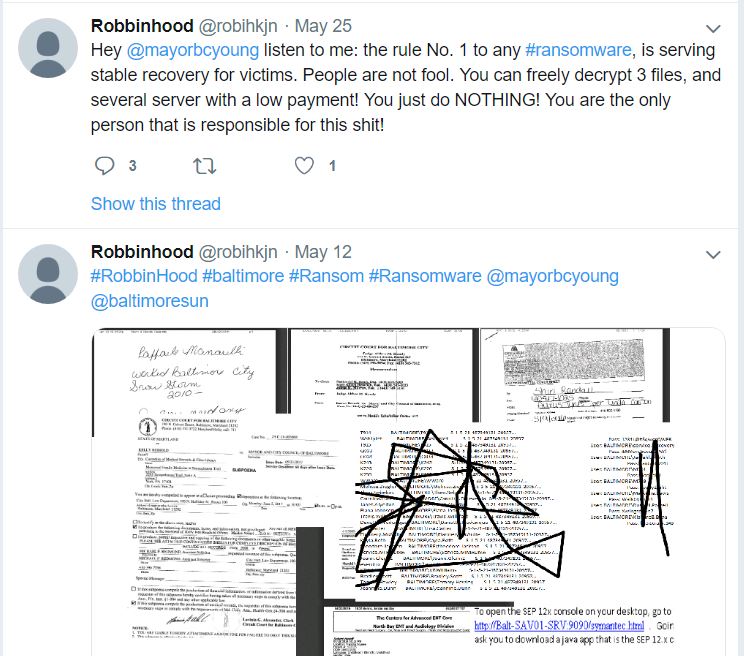
Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: 10 years of virtual dynamite: A high-level retrospective of ATM malware

cyber security: Hackers target Google Docs, Microsoft Sway to steal user credentials, IT Security News, ET CISO

LG Electronics Victim of Maze Ransomware Attack, Source Code Stolen: Report - Lebanon news - أخبار لبنان
Cybercriminals Exploit Coronavirus with Wave of New Scams WatchGuard's RSA Conference 2020 Recap Cyber Leads Global Business R