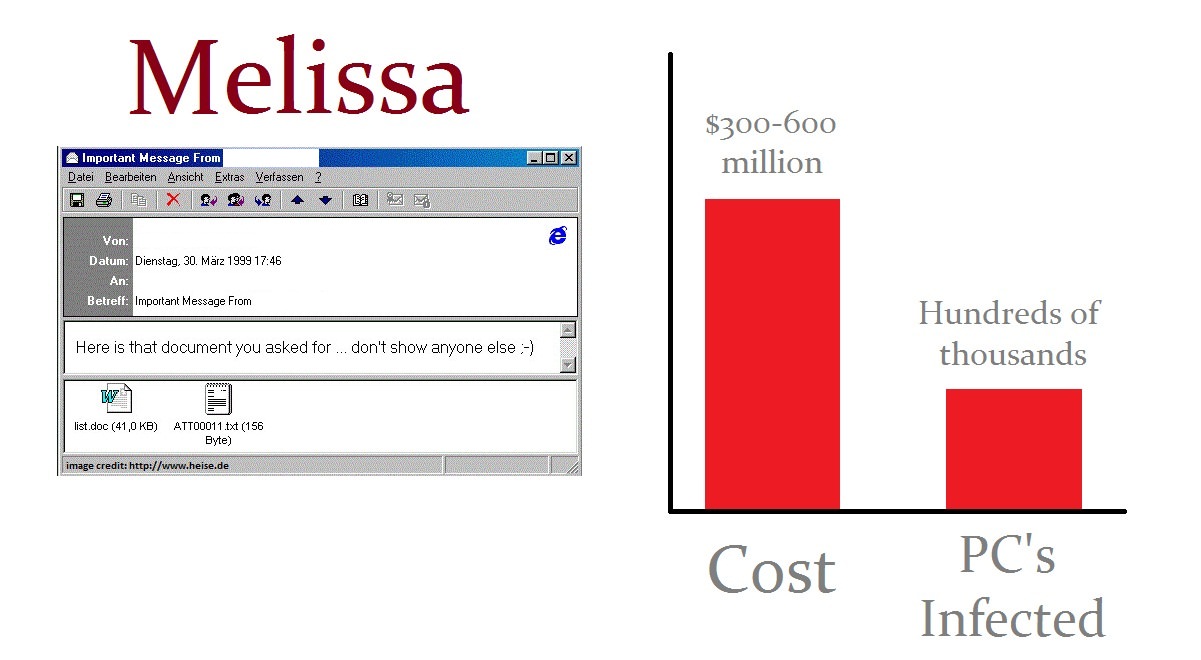
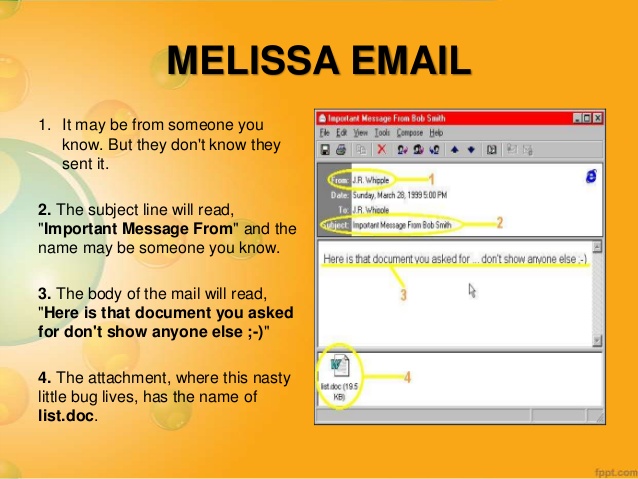
The largest cybersecurity breaches of the past three years, and their effects on companies | TechRepublic
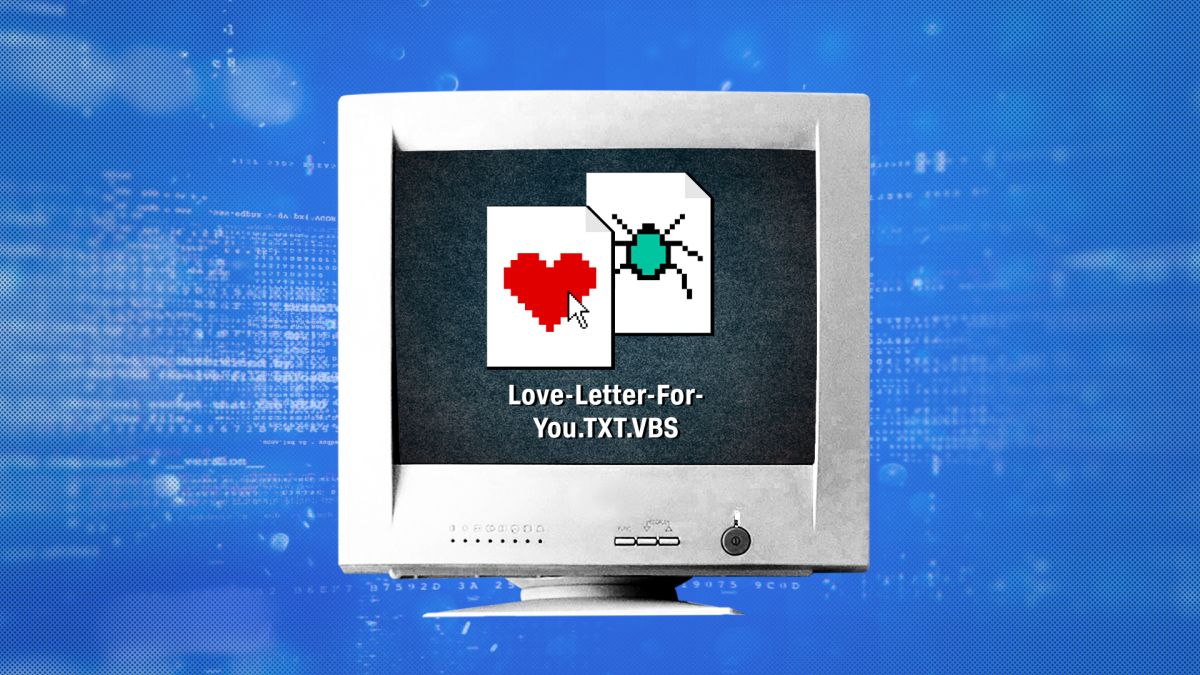
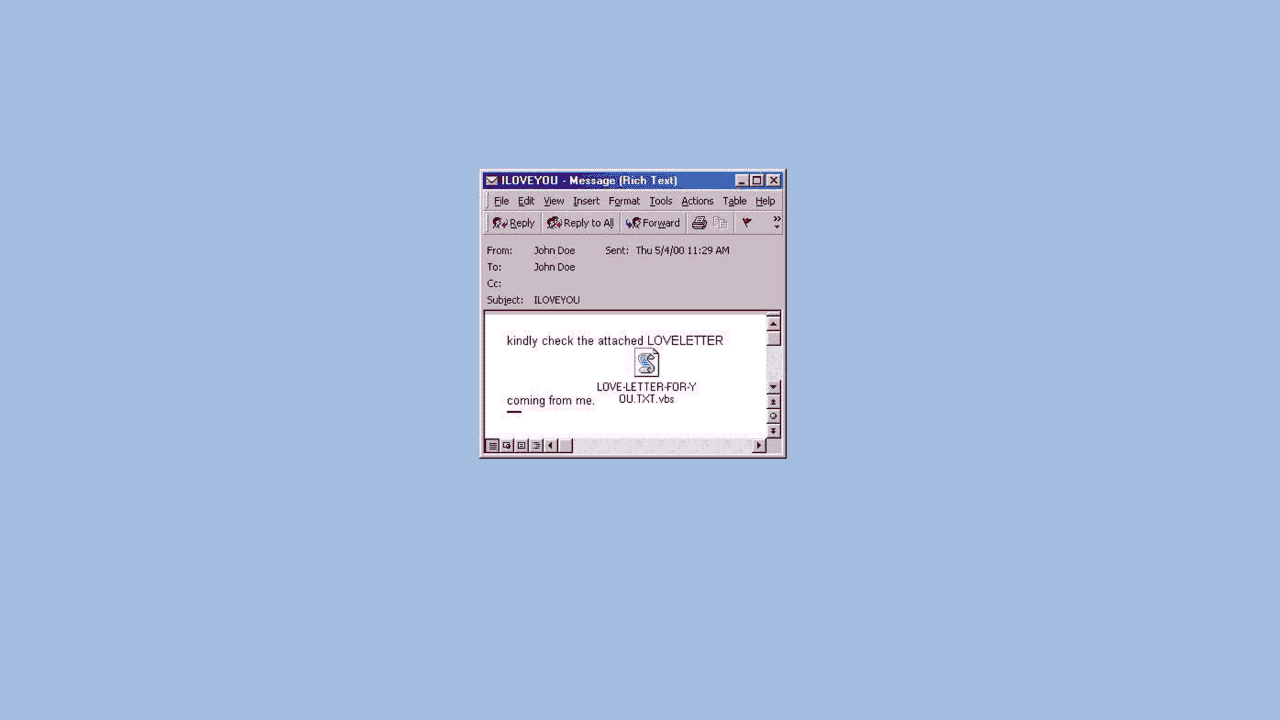
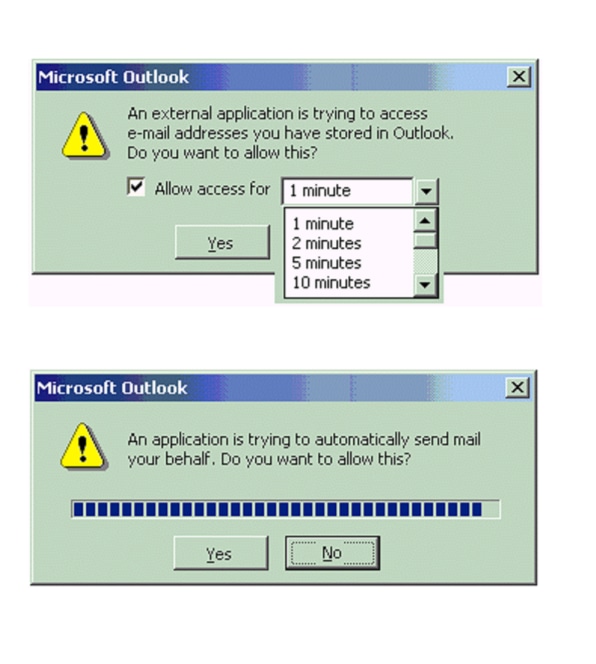
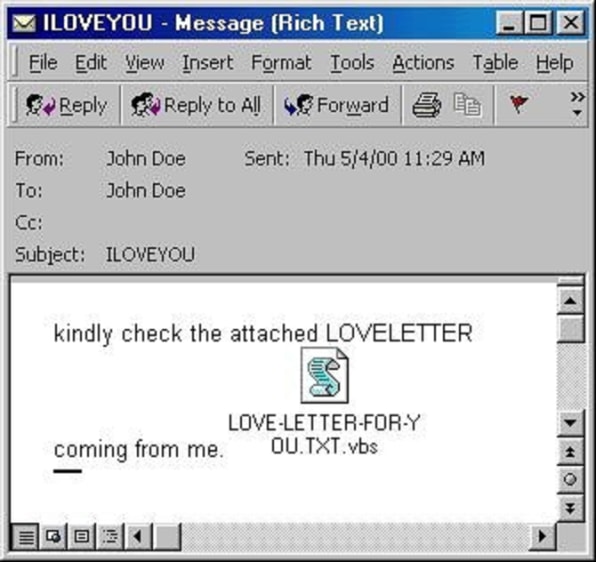
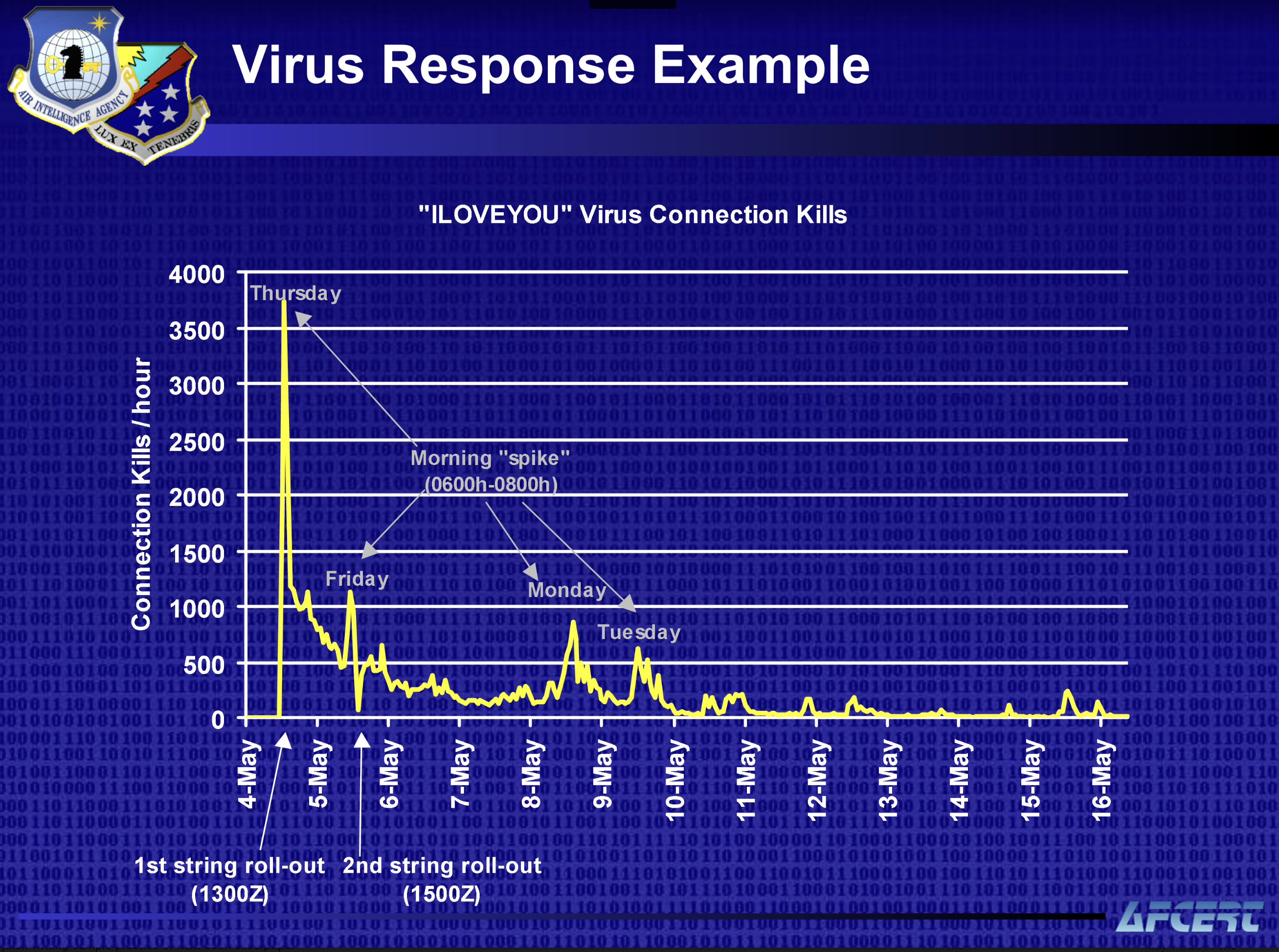
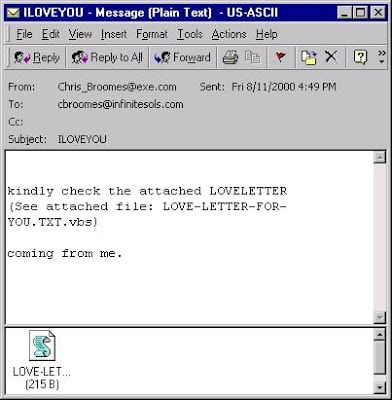
I love you': How a badly-coded computer virus caused billions in damage and exposed problems which remain 20 years on - CNN
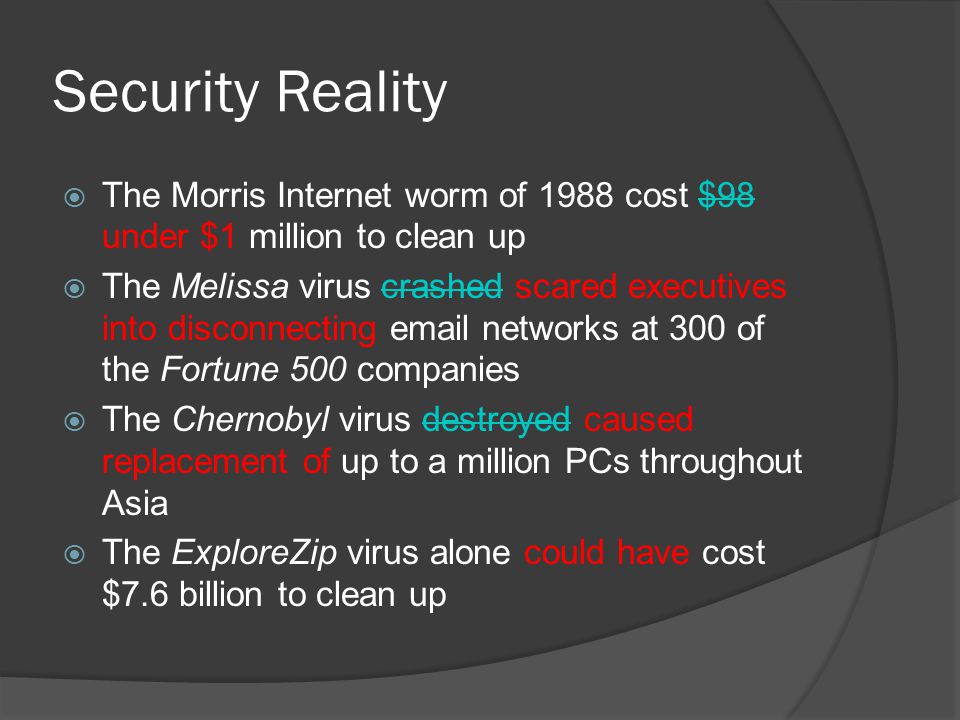
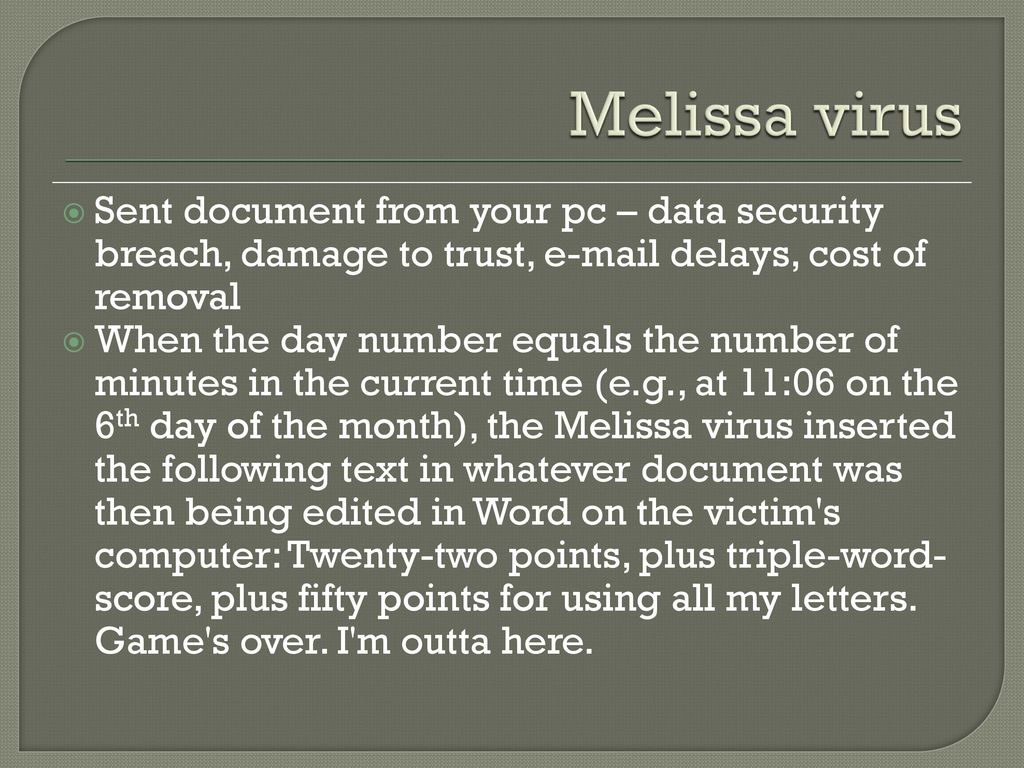
22 November Security and Privacy Security: the protection of data, networks and computing power Privacy: complying with a person's desires when. - ppt download

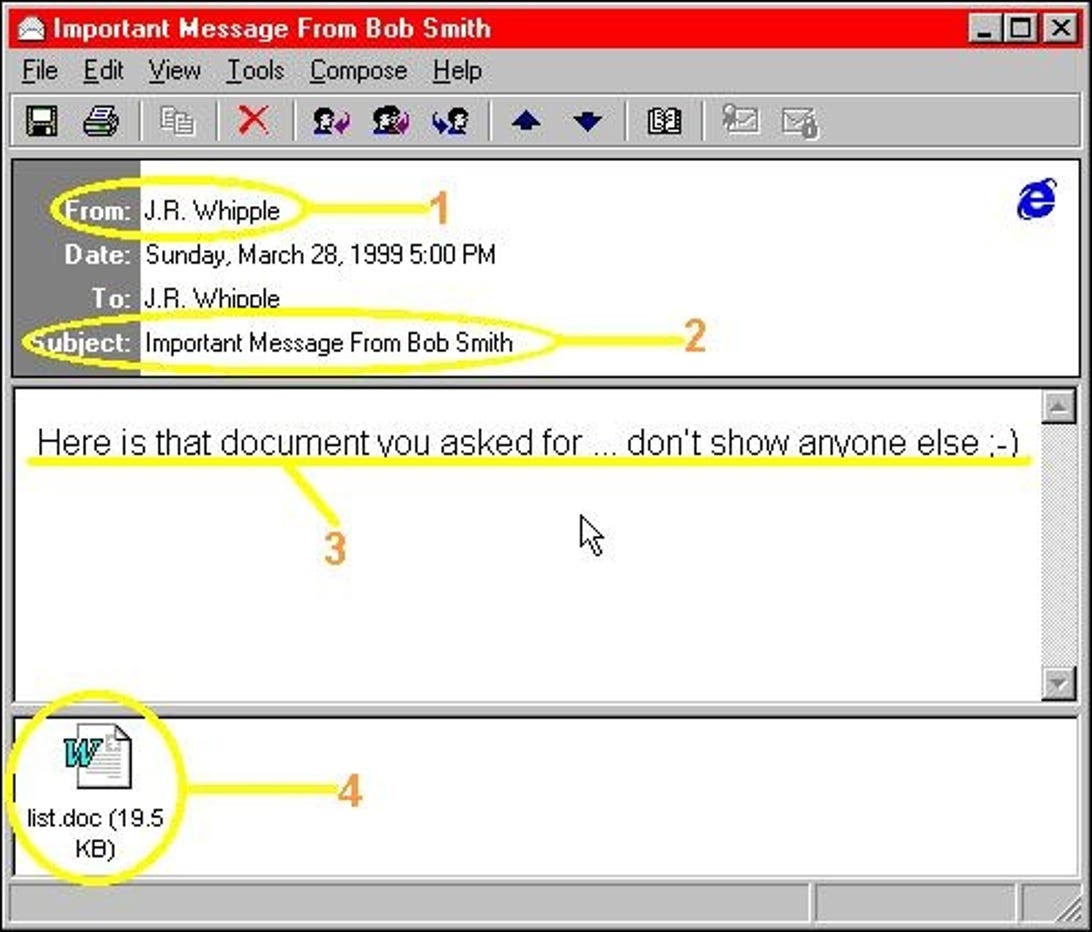
Social Engineering Abuses Sean Toh BJ Bayha. Overview What is Social Engineering? What does the survey say ? Case Studies −Case 1: Kevin Mitnick −Case. - ppt download